Password Security: The Ultimate Guide
Introduction
Almost all secure online services or platforms are protected using passwords. The task of creating these passwords is often left to the users. Although websites typically give requirements for their passwords, and sometimes even feedback on how strong it is, creating readable, unique, and safe passwords can be a difficult task. This guide will go over the properties and characteristics of a good password, delves into the process of password hacking and also offers a tool which can help you generate secure and unique passwords yourself. Welcome to "Password security: The ultimate guide"! First things first: It’s crucial to always use different, unique passwords for different websites or services. If you use the same password everywhere, you essentially put all your eggs in the same basket. If you use your bank password for some shady dropship website, and they get hacked or leak the password, it's not just that single account that is compromised, it is your bank account as well. Small variations of the same password are also ill-advised, since hackers can use simple logic to crack the variations as well (see "Password hacking"). You can actually quite accurately check whether or not this is the case for your e-mail adress via a website called "HaveIBeenPwned.com".
Password Security
Besides using different passwords for each use case, the security of the password itself needs to be sufficient as well. The length of the password is generally speaking the most important security feature it has. This is why essentially all services require a minimum password length. A longer password simply means more possible combinations of characters, making it harder for attackers to hack or brute force. A longer password isn't necessarily safe, however. If your password is 22 characters, but it is "Password123Password123", it will still be easy to hack. But for a randomly generated string like the passwords this website generates, attackers cannot use logic to crack it. They have to use a method called "Brute force". This essentially means guessing the password (or often rather the hashed version of a password) over and over again until you guess it correctly. Although possible, brute forcing is typically a worst-case scenario for attackers. Forcing attackers to resort to brute-forcing is the first step in creating a secure password. And you do this by being completely random. However, humans typically have trouble being completely random, and passwords usually end up being the names of objects in the room, or gibberish smashed on the keyboard. Both of these are easier to hack than completely random passwords. For example, even if you type gibberish by smashing your keyboard, attackers may use their knowledge about the proximity of different keys on the keyboard to guess the password (e.g. most people use the 'asdf' keys excessively when typing gibberish). Because humans have this problem with randomness, websites like these can be a great help (bookmark me).
Remembering your password
This randomness also poses a usability problem: remembering your passwords. From a usability perspective, passwords are a godawful concept. If they're easy to remember, they're not safe. And if they're safe, they're not easy to remember. There are different methods and tools you can use to help you remember your passwords, but they also all come with their own disadvantages. Writing them down on a piece of paper is a commonly used method. This does protect you against remote, online hackers, but has a ton of disadvantages too. The piece of paper can be assessible to people who have access to the computer, the piece of paper can be lost, you cannot read the handwriting, etc. There are online tools called password managers, which store all your passwords and are often able to generate random passwords as well, which they'll remember for you. They require a single master-passwords to access all of your smaller, unique passwords. This is typically a safe method of storing your passwords, and most browsers offer something like this (e.g. the "Remember me" button). There also exist third-party services that offer password managers. The disadvantages are that you still have to remember a long and complicated master-password, which essentially just moves the problem up one level. Another argument often used against this method is that you have to trust whoever offers you this service with all your passwords. If the password manager gets hacked, or "accidentally" leaks your passwords, you have lost them all and they are immediately in the hands of hackers. Security questions are commonly used as a back up tool, rather than an alternative. You can use these when you, for example, forgot your password. The problem is that they're not random, which is a fundamental requirement for a safe password and a recurring theme in this guide. Other people may also know the name of your first pet, for example. Since they are often used as a back-up for passwords, rather than an alternative, they do have the redeeming factor that they usually notify you per e-mail or text when somebody accessed your account via one of these questions. In the end, each method has its own advantages and disadvantages, and you'll have to decide for yourself which method best suits your situation.
Calculating Password Security
So, let's say that you've created a password which is completely random. How can you determine how safe such a password is? Well, given that it is totally random, you can use the average required brute force attempts. This is the average number of times an attacker will have to guess the password before guessing it correctly. The average required brute force attempts of any password can be calculated by the formula:
Where N equals the average required number of brute force attempts, C equals the length of the character set, and L equals the length of the password. For a password that only consists of numbers, the character set length is \(10\). Let's say we make a password with a length of \(3\). The first number can be \(0 - 9\), so that's \(10\) unique cases. The second number can be \(0 - 9\) too, again, \(10\) unique cases. But the combination of the first and second number is then \(10 * 10 - 100\). Add the third number and it becomes \(10 * 10 * 10\) or \(10^3 = 1000\) possible combinations. On average, whilst brute-forcing, you'll find the correct password halfway through. So, the average required brute force attempts for a password with length \(3\) and a character set length of \(10\) is \(\frac{10^3}{2} = 500\). Computers can make these calculations really fast and crack this password in a matter of milliseconds. Note that most attackers will attempt to brute-force a password systematically. Meaning that they will start at the first possible combination (character 1 \(*\) minimum password length) and work their way forward from there. Theoretically speaking, you could counter this by ensuring that your password will be one of the last ones to occur by starting and ending with a special character. However, this, in turn, can also be countered by the attacker by using the same logic. Plus, attackers will typically let the program finish, rather than stopping it, so even if you were the last one to occur in their attack, they will still find your password, making this a bad strategy. The abovementioned formula makes one critical assumption, however. Which is that it knows the length of your passwords. If attackers don't know the length of your password, they'll have to try combinations of different lengths. This greatly increases the number of average required brute force attempts, and changes the formula to:
Where N equals the average required number of brute force attempts, C equals the length of the character set, and s and e equal the lowest and highest possible password length respectively. This formula assumes that, on average, you'll find the correct password halfway through the set as well.
Our Password Generating Algorithm
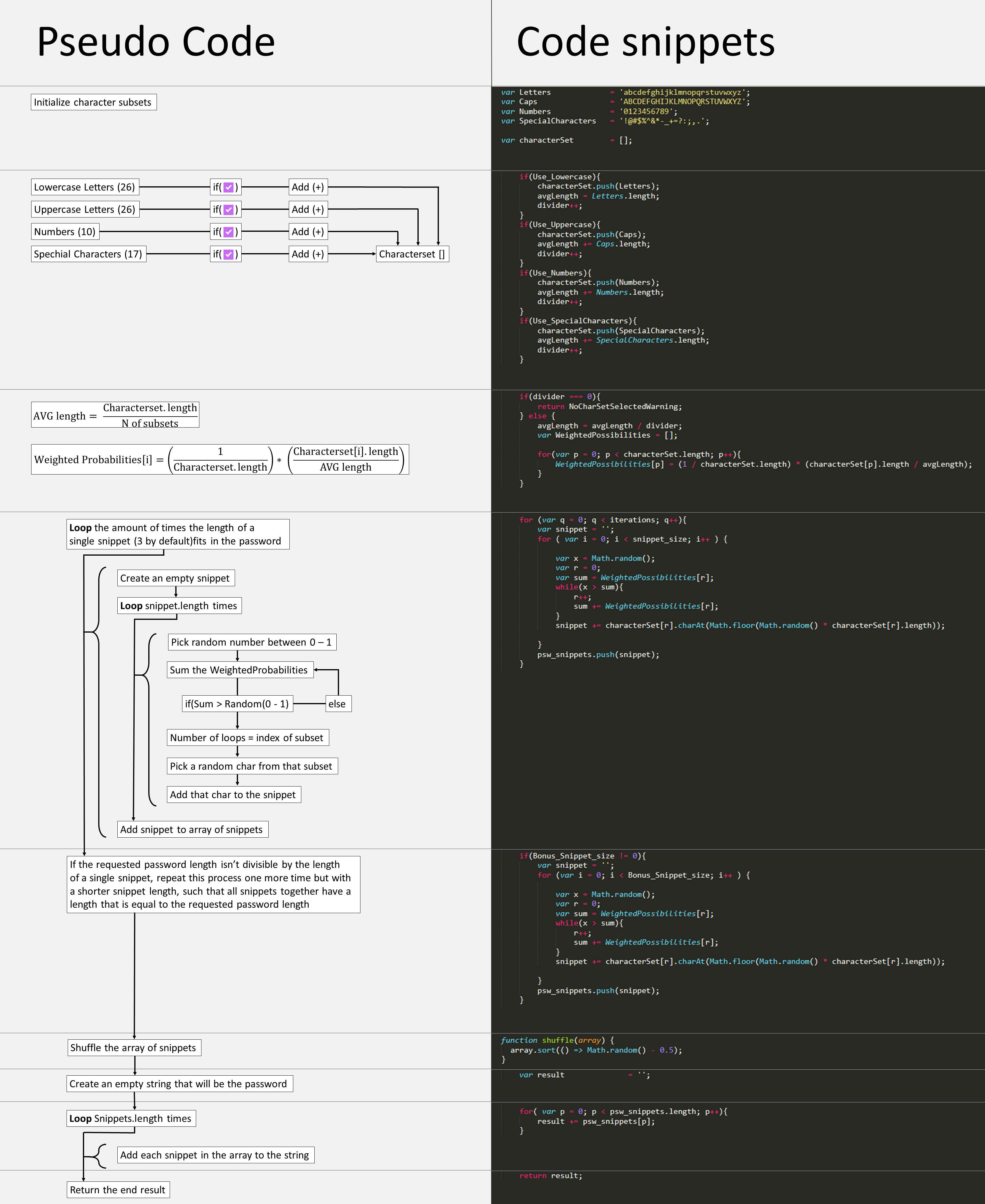
The password generator on this website has a total character set length of 79, given that you use all 4 possible components in your password. The possibility for a character from any given set to occur in your password is weighted, meaning that it's dependent on the length of the character set. For example: The set of lowercase letters has a length of 26, and the set of numbers only has a length of 10. If you were to pick a random set with equal probabilities, numbers and lowercase letters are equally likely to occur and on average your password will consist of 50% lowercase letters and 50% numbers. But since there are way less numbers than lowercase letters, the probability for any given number to occur is higher than the probability of any given lowercase letter to occur. Smart attackers can use this logic to reduce the average amount of required brute force attempts significantly. When you click on the generate password button, the password making algorithm will pick a character at random, using weighted probabilities. So that every single character has the exact same chance to occur in any given password. It will do this 3 times and create a so-called snippet, consisting of 3 characters. If the password length isn't a multiple of 3, it will add a shorter snippet using the same method. These snippets are then shuffled again, adding an extra layer of randomness. This isn't required, but since even the random functions in a computer aren't exactly random (although essentially, they are), layering them solves this problem.
Note that not all (or any even) characters from a given set necessarily have to appear in a given password in order to be counted in a formula. Even if a character doesn’t appear in a certain password, there was a probability that it would have, so mathematically speaking, the password is just as secure as if the character were there. This is actually done on purpose, since any logic like "Every set must contribute at least one character to the password" can be used by hackers to greatly decrease the number of average required brute force attempts. Knowing the formula for average required brute force attempts, you might realize that the more different, potential characters you use, the harder your password is to crack. And you're absolutely right. So why does the set of special characters on this website only has a length of 17, even though there are much more special characters available? Well, this is a point where user friendliness was chosen over absolute security. Some websites may not be able to handle these special characters in their code, and may not accept a password that contains them, or worse, process it incorrectly. In order to prevent this, we only generate passwords that contain some basic special characters like '!', '@', and '?'. But despite this compromise, any password with a proper length from this website is still absolutely safe to use. But if whatever website you're using the password for allows it, feel free to add special characters yourself. The rarer the better. Characters like 'Ω;', 'ξ' or '∉' appear in almost no hacker's character set, and therefore make your password nearly uncrackable.
Password Hacking
Password hacking can take many different forms. This also includes less-technical methods like phishing and social engineering. One of the most effective strategies is typically to use a dictionary (dictionary attack). A dictionary, in this context, is a large list of potential passwords. The so-called "RockYou" list is a very commonly used example. It contains 14,341,564 unique passwords, used in 32,603,388 real accounts, which were leaked when a company called "RockYou" was hacked in 2009. This list is publicly available online and can be found by a quick Google search. Dictionary attacks and other similar attacks are used when a database full of accounts / passwords has been leaked. These passwords are typically not stored in plain text (god forbid if you store passwords in plain text), but are hashed instead. Hashing is a method of turning a certain string of text, like a password, into a long, appearantly random string of text. But this process isn't random, and every unique string generates the exact same unique string. The whole idea behind hashing is that it's a one way process. It's very quick and easy to create a hash from a password, but near impossible to get the original password back from a hash. The idea behind this principle is that it's very easy to multiply 2 factors, but very hard to find which factors can multiply into a certain number (e.g. 832 * 234 = 194688, quick and easy, but which 2 factors multiply into 194688? Difficult question with many answers). So the typical approach is to use the hashing algorithm on a set of possible passwords, like the RockYou list, and see if the resulting hashes match the hashes in the database. This is also why it's a bad idea to have "Password123" as your password, since the hash for this password has long been cracked. These passwords are also combined with a set of rules. There rulesets may differ for any given platform and usually depend on the password requirements they pose. Rulesets can be made by the attackers themselves. Of course, the rules are written differently, using code instead of natural language. Example rules may include things like: "Try the same password but with an uppercase letter at the start", "Try the same password but with a '!' at the end", append the first two letters of the website name to the password", "Add the date on which this user account was created to the beginning of the password" or "Replace all occurrences of the letter 'E' with the number '3'". These rule sets are a tool for attackers to incorporate some logic into their attacks. And the best counter against this is to be totally random, like the passwords generated by this website. As you can imagine, adding these rules greatly increases the amount of times an attacker needs to loop over the dictionary, but also increases the number of passwords the attacker will crack. Most hackers will realize that it's impossible to hack every single password in a set. So typically, you don't need to be absolutely uncrackable, you just don't need to be among the easier ones. That being said, it's better to be safe than sorry.
Last Remarks
This article has primarily focused on protecting against brute force attacks, acting as if that is the only tool that hackers have left if your password is strong and random, but that isn't true. Somebody might also monitor your browser, or the data you send via a non-secure website that doesn't use SSL or TSL encryption. Somebody might even just be looking at your screen when you enter your password. Your passwords are just one link in a chain of protection, so even the strongest passwords become irrelevant if you send them via an unsecure connection. Luckily, most people aren’t out to get you. The chances that somebody is going to spend weeks trying to hack the password to your 15 follower twitter account aren’t that big. And nobody benefits from unnecessary paranoia. The last tip I'll give you is to change your passwords regularly. Every year or so is a good interval, but it depends on the service the password is for as well. Absolutely do change your password when you notice weird activity on your account or receive e-mails that you've logged in via another device which isn't yours.